- Bitcoin
- Ethereum
- Hemi
- Learn Center
- Security
- September 4, 2024
Can Hemi’s Security Model Be Applied to Other Blockchains?
Hemi’s Proof-of-Proof (PoP) consensus model provides the network with superfinality by using Bitcoin’s security infrastructure. But can this protocol be used with other blockchains?

To explore how other blockchain protocols can inherit Bitcoin’s security through Hemi, we need to look at how PoP operates and achieves superfinality.
How PoP Works
Proof-of-Proof (PoP) is a consensus mechanism designed to inherit the robust security of Bitcoin’s Proof-of-Work (PoW) and extend it to other blockchains, particularly those integrated with the Hemi Network.
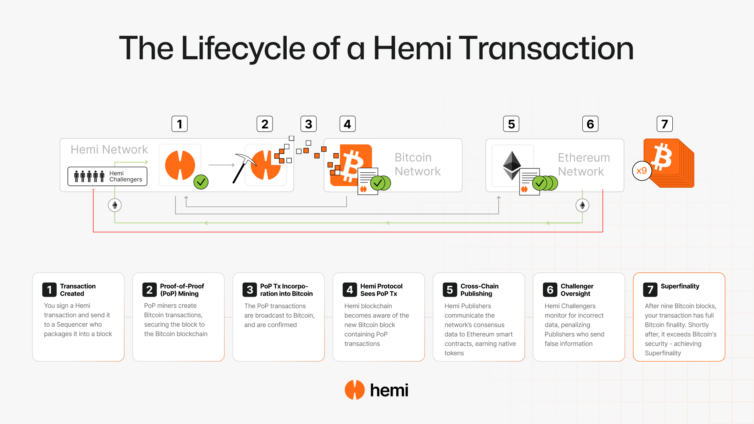
Here’s how it works:
1. State Publication to Bitcoin
PoP involves the periodic publication of blockchain state data from the Hemi Network (or other blockchains using PoP) to the Bitcoin blockchain. By embedding this data in Bitcoin transactions, PoP ensures that the security of Bitcoin’s PoW is extended to the chain that published the data.
2. Decentralized Mining and Publication
PoP relies on a network of PoP miners who are responsible for building these Bitcoin transactions that contain the state data. These miners create transactions that encode the Hemi block headers or other blockchain data into Bitcoin transactions. These transactions are then broadcast to the Bitcoin network, where they are included in Bitcoin blocks.
3. Security and Finality
Once a Hemi block header or other state data is confirmed on the Bitcoin blockchain, it gets the same level of security as Bitcoin itself. Since Bitcoin’s PoW is one of the most secure consensus mechanisms, this process significantly enhances the security of published data. This means that to alter the Hemi state data recorded on Bitcoin, an attacker would need to perform a 51% attack on both Bitcoin and Hemi simultaneously, which is extremely expensive and technically difficult.
4. Fork Resolution and Attack Resistance
If there is a blockchain fork, PoP helps resolve the legitimate chain by referring to the state data that has been published and confirmed on the Bitcoin blockchain. If an attacker tries to create a competing chain or reorganize the existing one, they would need to publish their altered state data to Bitcoin and ensure it gains enough confirmations to override the original data. Given Bitcoin’s high security, this attack is highly unlikely to succeed, providing strong resistance against reorganization attacks.
5. Superfinality
PoP introduces the concept of “superfinality,” where a block on the Hemi Network (or any other blockchain using PoP) becomes fully immutable after a specific number of Bitcoin confirmations. Once a Hemi block is anchored in Bitcoin and gains several confirmations, it becomes mathematically impossible to reverse it without compromising Bitcoin itself. This provides a higher level of finality than what is typically achievable on other blockchains.
Using PoP With Other Blockchains
Hemi’s security model offers a robust framework that can be extended to secure other blockchains. By leveraging the security of Bitcoin’s Proof-of-Work (PoW), Hemi’s network achieves high levels of security and finality. This security model is not limited to Hemi alone; it can be applied to other blockchains through Hemi’s modular architecture, providing these networks with the same level of security traditionally reserved for Bitcoin.
One of the ways Hemi extends its security model to other blockchains is through its forthcoming Chainbuilder offering. Any blockchain, regardless of its native consensus mechanism, will be able to integrate with Hemi to inherit Bitcoin’s security. This is achieved by incorporating Hemi’s PoP system into their existing consensus protocols. Through this integration, blockchains can publish their consensus state to the Hemi Network, which then aggregates these states and secures them by anchoring them to Bitcoin’s blockchain. This process ensures that any attempt to reorganize or attack the blockchain would require a simultaneous 51% attack on Bitcoin itself, which is economically and computationally difficult.
Hemi’s Chainbuilder enables other blockchains to launch custom ecosystem chains that can use Hemi’s security model while maintaining their unique characteristics. These chains can be tailored with different execution, consensus, and data availability layers to optimize for specific use cases, whether they require high throughput, low cost, or enhanced decentralization. Regardless of these customizations, Hemi’s security model ensures that all transactions on these hChains are protected by Bitcoin’s PoW, providing an additional layer of trust and resilience.
To find out more about how Hemi achieves superfinality with PoP consensus by inheriting the robust security of Bitcoin (or any other blockchain network you wish), read the whitepaper and the relevant documentation or stop by the team’s Discord.